How should I prepare to take the EC-COUNCIL certification test?I would like to recommended Pass4itsure, they have excellent Exam dumps with latest and relevant questions and answers in PDF files.Visit now https://www.pass4itsure.com/ec-council.html to get EC-COUNCIL exam study material.You can get free EC-COUNCIL exam dumps here.

Latest EC-COUNCIL List
Latest Valid EC-COUNCIL exam dumps, 312-49,312-49V9, 312-50V10
Latest Valid 312-49 List
About the Exam
- Number of Questions: 150
- Test Duration: 4 Hours
- Test Format: Multiple Choice
- Test Delivery: ECC EXAM
- Exam Prefix: 312-49 (ECC EXAM)
In order to maintain the high integrity of our certifications exams, EC-Council Exams are provided in multiple forms (I.e. different question banks). https://www.eccouncil.org/programs/computer-hacking-forensic-investigator-chfi/
Latest 312-49 exam practice questions (1-5)
QUESTION 1
Which federal computer crime law specifically refers to fraud and related activity in connection with access devices like
routers?
A. 18 U.S.C. 1029
B. 18 U.S.C. 1362
C. 18 U.S.C. 2511
D. 18 U.S.C. 2703
Correct Answer: A
QUESTION 2
You are assigned to work in the computer forensics lab of a state police agency. While working on a high profile criminal
case, you have followed every applicable procedure, however your boss is still concerned that the defense attorney
might question whether evidence has been changed while at the lab. What can you do to prove that the evidence is the
same as it was when it first entered the lab?
A. make an MD5 hash of the evidence and compare it with the original MD5 hash that was taken when the evidence first
entered the lab
B. make an MD5 hash of the evidence and compare it to the standard database developed by NIST
C. there is no reason to worry about this possible claim because state labs are certified
D. sign a statement attesting that the evidence is the same as it was when it entered the lab
Correct Answer: A
QUESTION 3
Which of the following email headers specifies an address for mailer-generated errors, like “no such user” bounce
messages, to go to (instead of the sender\\’s address)?
A. Mime-Version header
B. Content-Type header
C. Content-Transfer-Encoding header
D. Errors-To header
Correct Answer: D
QUESTION 4
Which of the following tool captures and allows you to interactively browse the traffic on a network?
A. Security Task Manager
B. Wireshark
C. ThumbsDisplay
D. RegScanner
Correct Answer: B
QUESTION 5
Which MySQL log file contains information on server start and stop?
A. Slow query log file
B. General query log file
C. Binary log
D. Error log file
Correct Answer: D
More 312-49 exam practice questions please visit: https://www.pass4itsure.com/312-49.html
[PDF] Free 312-49 pdf dumps download from Google Drive:
https://drive.google.com/open?id=1JORBYMYtl3mxZA6J37OrYjP6DoD3JUgp
Latest Valid 312-49V9 List
About the Exam
“ECCouncil Computer Hacking Forensic Investigator (V9) Exam”, also known as 312-49v9 exam, is a EC-Council Certification.
Latest 312-49v9 exam practice questions (1-5)
QUESTION 1
Which of the following statements is not a part of securing and evaluating electronic crime scene checklist?
A. Locate and help the victim
B. Transmit additional flash messages to other responding units
C. Request additional help at the scene if needed
D. Blog about the incident on the internet
Correct Answer: D
QUESTION 2
Daryl, a computer forensics investigator, has just arrived at the house of an alleged computer hacker. Daryl takes
pictures and tags all computer and peripheral equipment found in the house. Daryl packs all the items found in his van
and takes them back to his lab for further examination. At his lab, Michael his assistant helps him with the investigation.
Since Michael is still in training, Daryl supervises all of his work very carefully. Michael is not quite sure about the
procedures to copy all the data off the computer and peripheral devices. How many data acquisition tools should
Michael use when creating copies of the evidence for the investigation?
A. Two
B. One
C. Three
D. Four
Correct Answer: A
QUESTION 3
Which of the following reports are delivered under oath to a board of directors/managers/panel of jury?
A. Written informal Report
B. Verbal Formal Report
C. Written Formal Report
D. Verbal Informal Report
Correct Answer: B
QUESTION 4
If you see the files Zer0.tar.gz and copy.tar.gz on a Linux system while doing an investigation, what can you conclude?
A. The system files have been copied by a remote attacker
B. The system administrator has created an incremental backup
C. The system has been compromised using a t0rn rootkit
D. Nothing in particular as these can be operational files
Correct Answer: C
QUESTION 5
You just passed your ECSA exam and are about to start your first consulting job running security audits for a financial
institution in Los Angeles. The IT manager of the company you will be working for tries to see if you remember your
ECSA class. He asks about the methodology you will be using to test the company\\’s network. How would you
answer?
A. IBM Methodology
B. Microsoft Methodology
C. Google Methodology
D. LPT Methodology
Correct Answer: D
More 312-49v9 exam practice questions please visit:
https://www.pass4itsure.com/312-49v9.html
[PDF] Free 312-49v9 pdf dumps download from Google Drive:
https://drive.google.com/open?id=1KbsVTH-iE8Vet-SWnkQMmPd-XKqCxio7
Latest Valid 312-50V10 List
About the Exam
The 312-50v10 or as it’s also known, the Certified Ethical Hacker v10 Exam, like all tests, there is a bit of freedom on ECCouncil’s part to exam an array of subjects.
Latest 312-50V10 exam practice questions (1-5)
QUESTION 1
Which of the following is the successor of SSL?
A. TLS
B. RSA
C. GRE
D. IPSec
Correct Answer: A
Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), both of which are frequently referred
to as \\’SSL\\’, are cryptographic protocols that provide communications security over a computer network. References:
https://en.wikipedia.org/wiki/Transport_Layer_Security
QUESTION 2
An attacker tries to do banner grabbing on a remote web server and executes the following command.
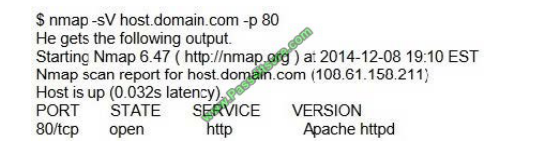
Service detection performed. Please report any incorrect results at http://nmap.org/submit/.
Nmap done: 1 IP address (1 host up) scanned in 6.42 seconds
What did the hacker accomplish?
A. nmap can\\’t retrieve the version number of any running remote service.
B. The hacker successfully completed the banner grabbing.
C. The hacker should\\’ve used nmap -O host.domain.com.
D. The hacker failed to do banner grabbing as he didn\\’t get the version of the Apache web server.
Correct Answer: B
QUESTION 3
You are a security officer of a company. You had an alert from IDS that indicates that one PC on your Intranet is connected to a blacklisted IP address (C2 Server) on the Internet. The IP address was blacklisted just before the alert.
You are staring an investigation to roughly analyze the severity of the situation. Which of the following is appropriate to
analyze?
A. Event logs on the PC
B. Internet Firewall/Proxy log
C. IDS log
D. Event logs on domain controller
Correct Answer: B
QUESTION 4
Low humidity in a data center can cause which of the following problems?
A. Heat
B. Corrosion
C. Static electricity
D. Airborne contamination
Correct Answer: C
QUESTION 5
Which of the following is used to indicate a single-line comment in structured query language (SQL)?
A. –
B. ||
C. %%
D. \\’\\’
Correct Answer: A
More 312-50V10 exam practice questions please visit:
https://www.pass4itsure.com/312-50v10.html
[PDF] Free 312-50V10 pdf dumps download from Google Drive:
https://drive.google.com/open?id=1zLaPRgp30J5I-Q2DVogcIH_hSP9RwkN1
ECCouncil Exams Related
Pass4itsure Discount Code(2020)

Pass4itsure tips!

Summarize:
Accurate learning materials and proper practice, you can crack the exam with excellent results. https://www.pass4itsure.com/ec-council.html help you!